DotEnv File
Environment variables are used to store sensitive data such as API keys, tokens, and configuration settings outside the source code. This helps keep your code secure and makes it easier to manage different settings for various environments (e.g., local, staging, production). In Bruno, environment variables can be managed through.env files.
DotEnv File for Secret Management
In Bruno, you can store your secrets (e.g., API keys, JWT tokens) in a.env file located at the root of your collection folder. This approach is inspired by how developers typically manage secrets in their codebase.
Folder Structure Example
Below is an example folder structure for your collection:Creating and Using the .env File
-
Create a
.envfile manually in the root of your collection folder. This file will store your sensitive environment variables. -
Define your secrets in the
.envfile. For example:
showLineNumbers
process.env object.
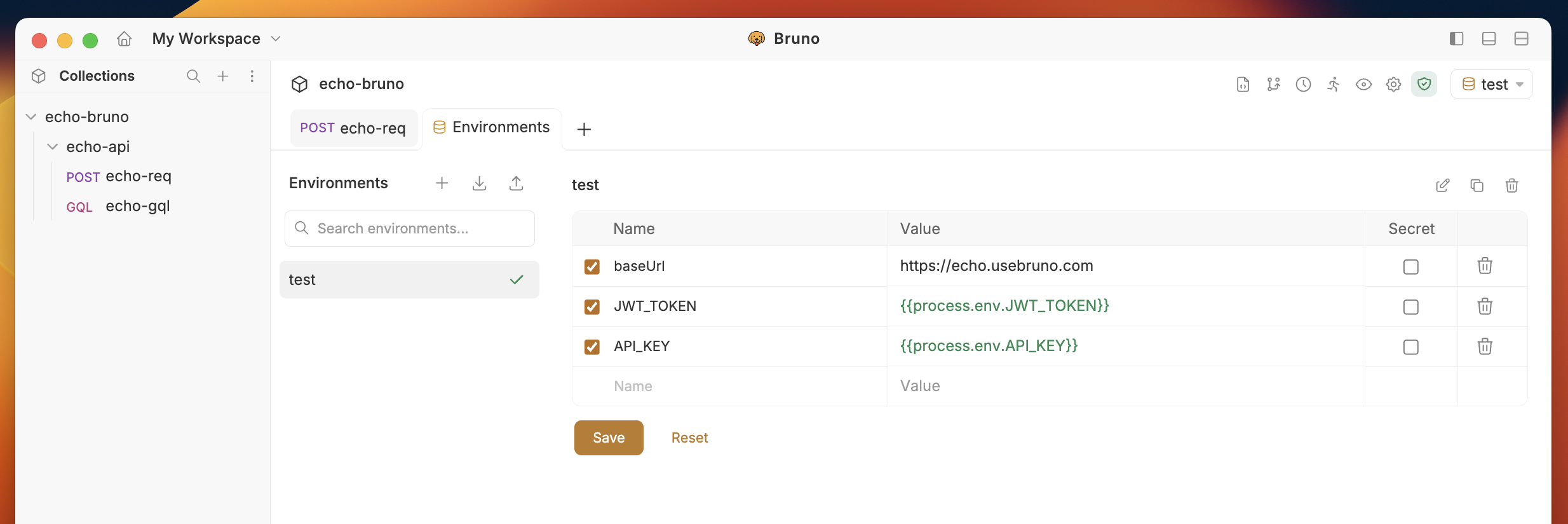
process.env.<secret-name>.
Your environment file at environments/local.bru would look like
JWT_TOKEN secret from the .env file is referenced using process.env.JWT_TOKEN. This will be replaced with the actual value of JWT_TOKEN when the collection is executed.
Managing Secrets
-
Always add the
.envfile to your.gitignorefile to ensure secrets are not accidentally pushed to version control. -
If you need to share the structure of your environment variables with other developers, create a
.env.samplefile without actual secret values.
Handling Variables with Dots
When using environment variables that contain dots in their names, use square bracket notation:Manage Environment Credentials
Bruno v3.1.0: You can now create, view, and delete environment variables directly from Bruno at the workspace level without manually editing
.env files.Accessing Environment Variables
- Navigate to Workspace → Global Environment section
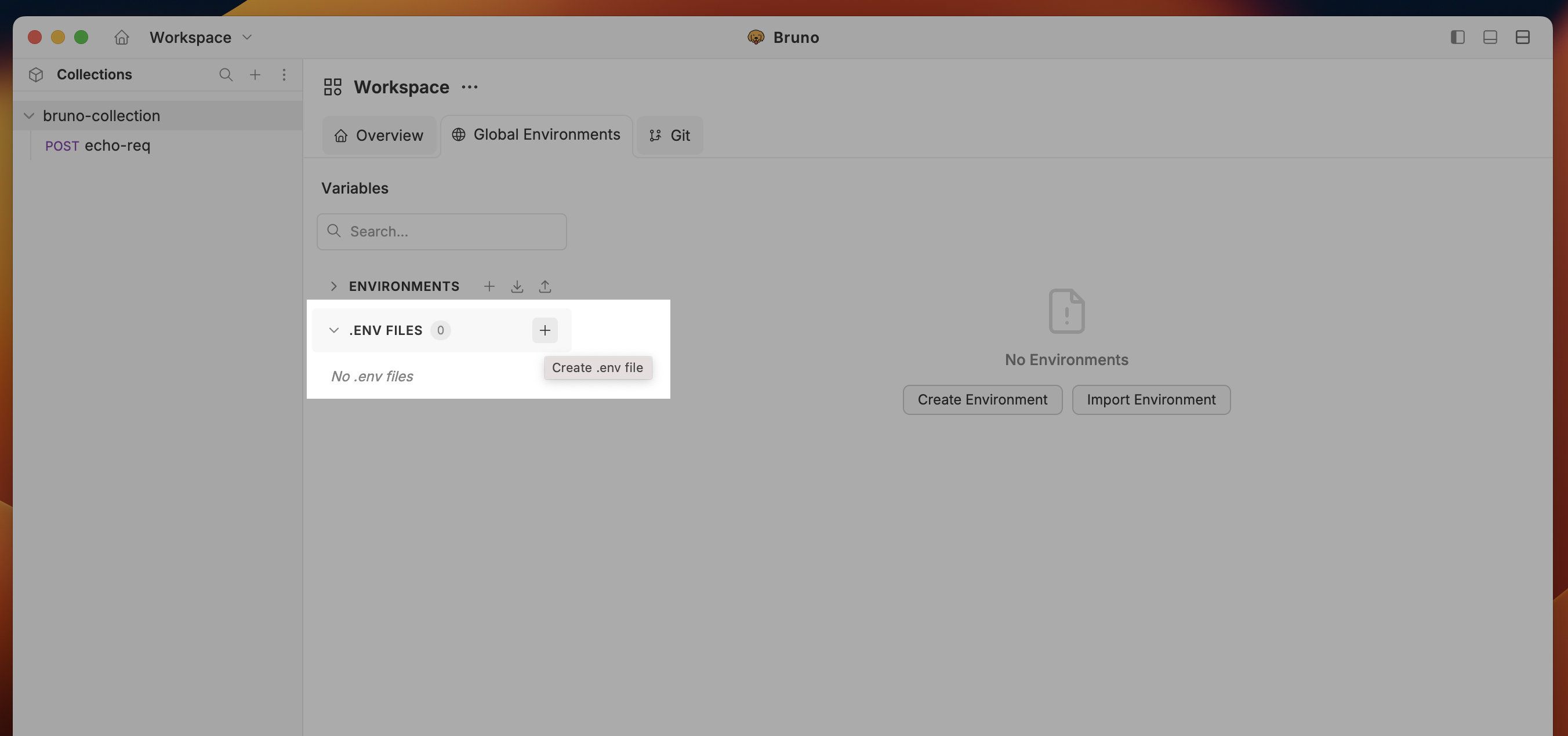
- Create or edit environment variables with your credentials
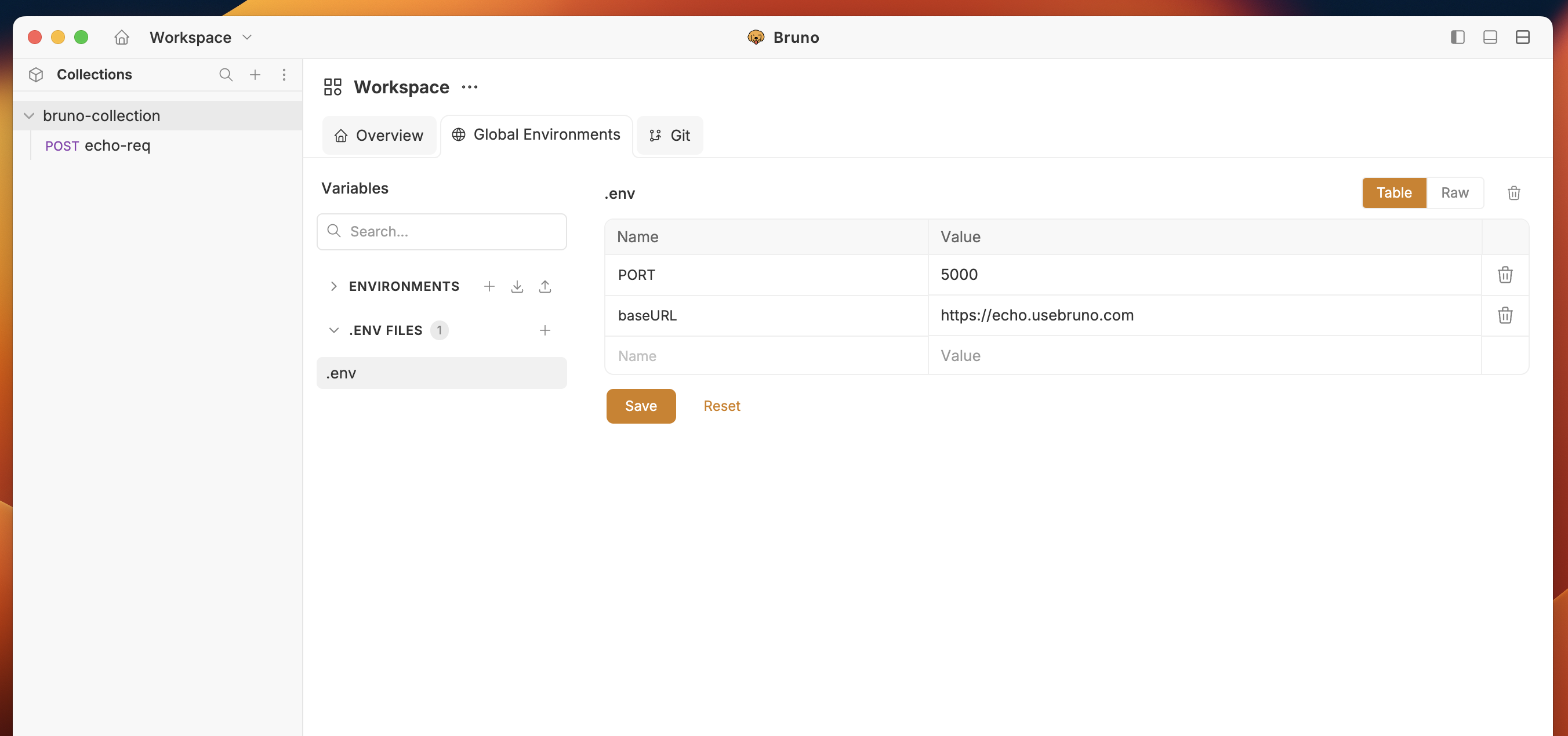
- Use these variables across all collections in your workspace using
{{process.env.<variable-name>}}syntax.
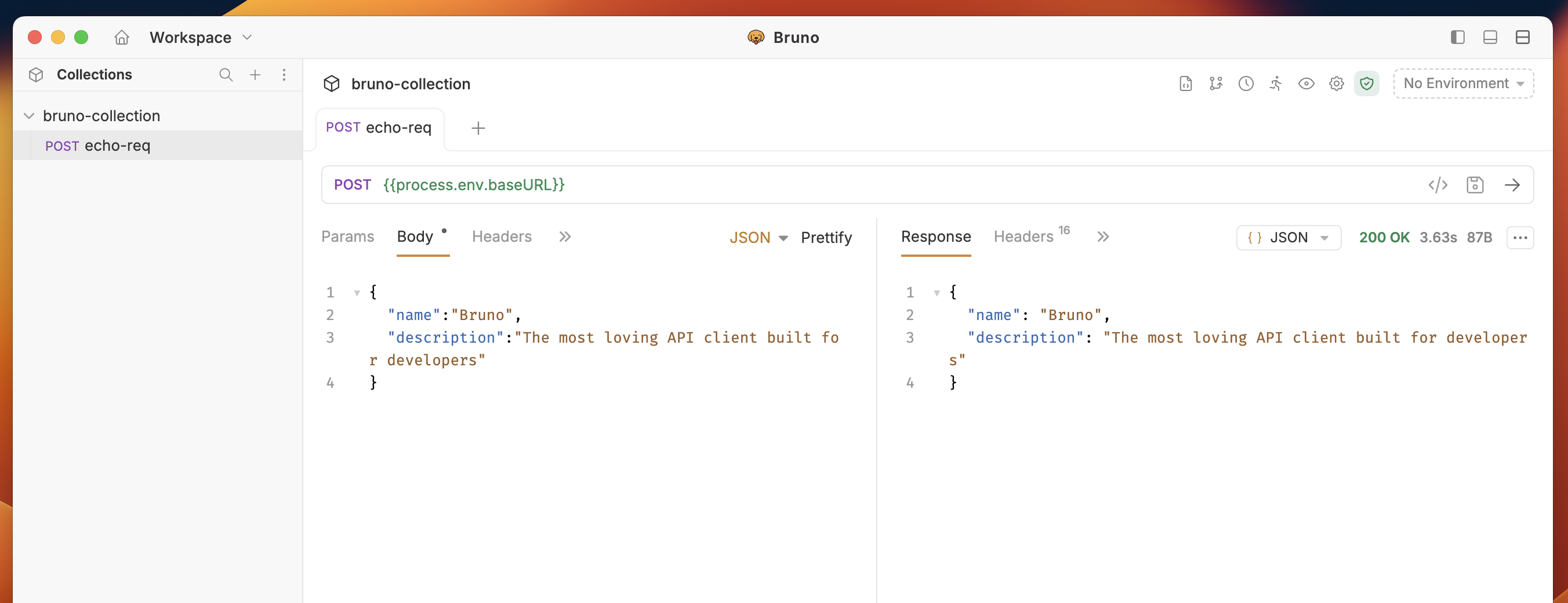
.env files while maintaining the same security and accessibility benefits.