Configure SAML SSO with Okta
This guide walks you through configuring SAML Single Sign-On for Bruno using Okta as your identity provider.
Before you begin, make sure you have completed the prerequisites and have admin access to both Okta and the Bruno License Portal.
Configure SSO in Bruno
Before configuring a SAML application in Okta, first configure SSO in Bruno.
- Log in to the Bruno License Portal
- Navigate to Settings → SSO in the left sidebar
-
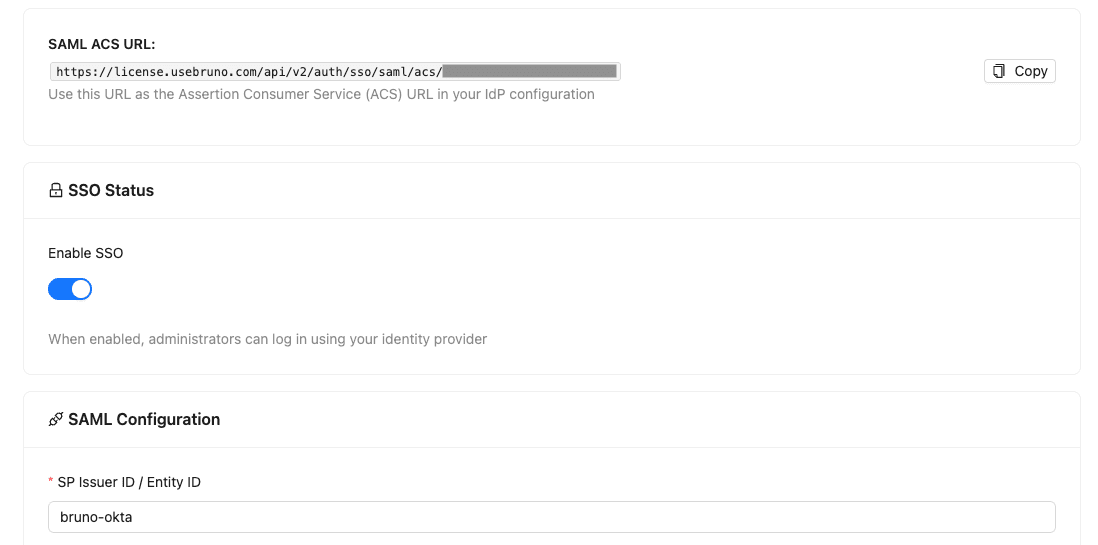
Toggle the Enable SSO switch on
-
Note the following values (you’ll need these when configuring Okta):
- SAML ACS URL: Copy this URL exactly as shown in Bruno
- SP Issuer ID / Entity ID: Set your own unique identifier (e.g.,
bruno-sso,bruno-okta,your-company-bruno, etc.)
Keep this page open in a separate tab - you’ll return here after configuring Okta to complete the Bruno SSO setup.
Configure SSO with Okta
Step 1: Create a New SAML Application
- Log in to your Okta Admin Console
- Navigate to Applications → Applications in the left sidebar
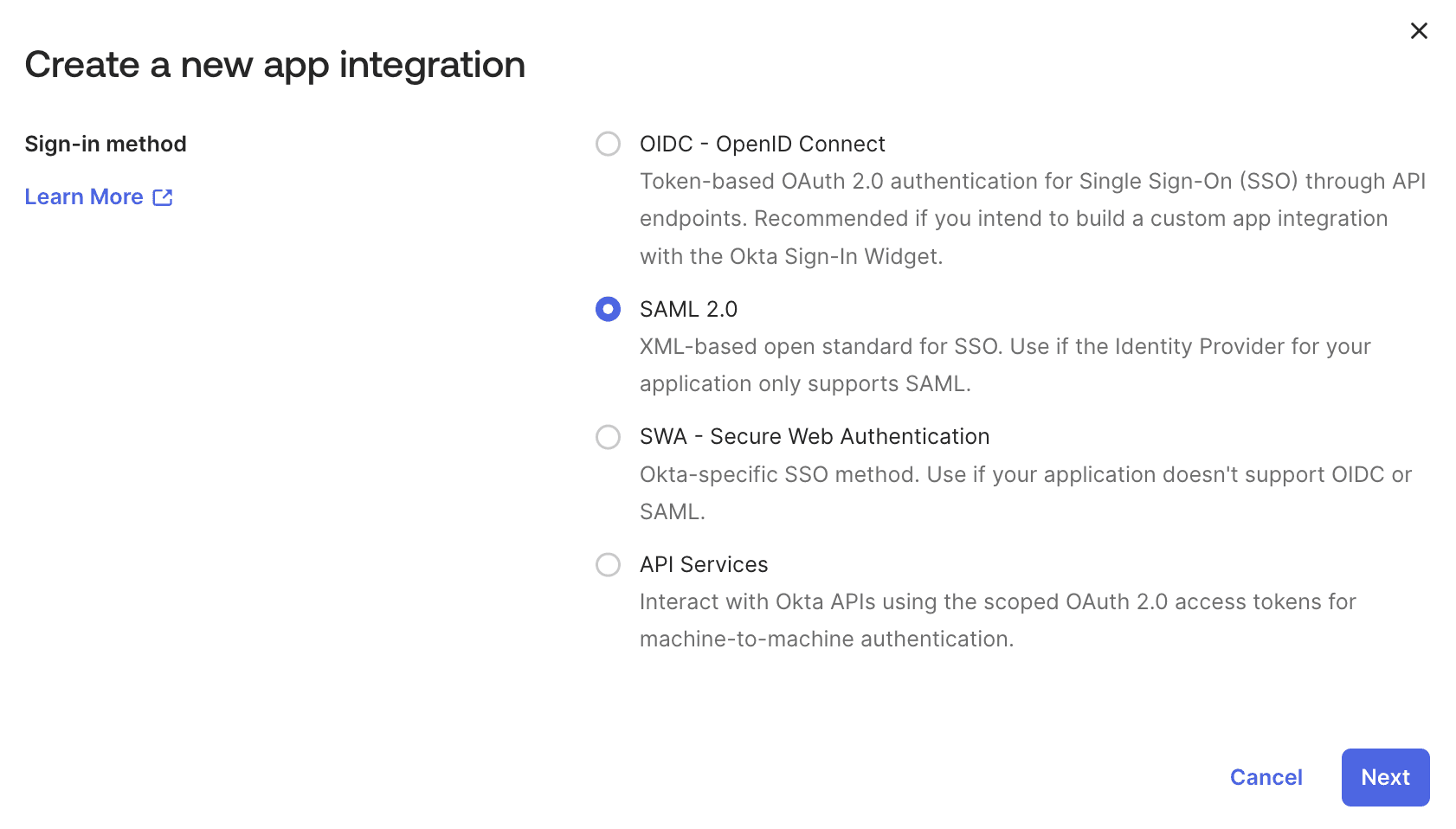
- Click Create App Integration

- Select SAML 2.0 as the sign-in method
- Click Next
Step 2: Configure General Settings
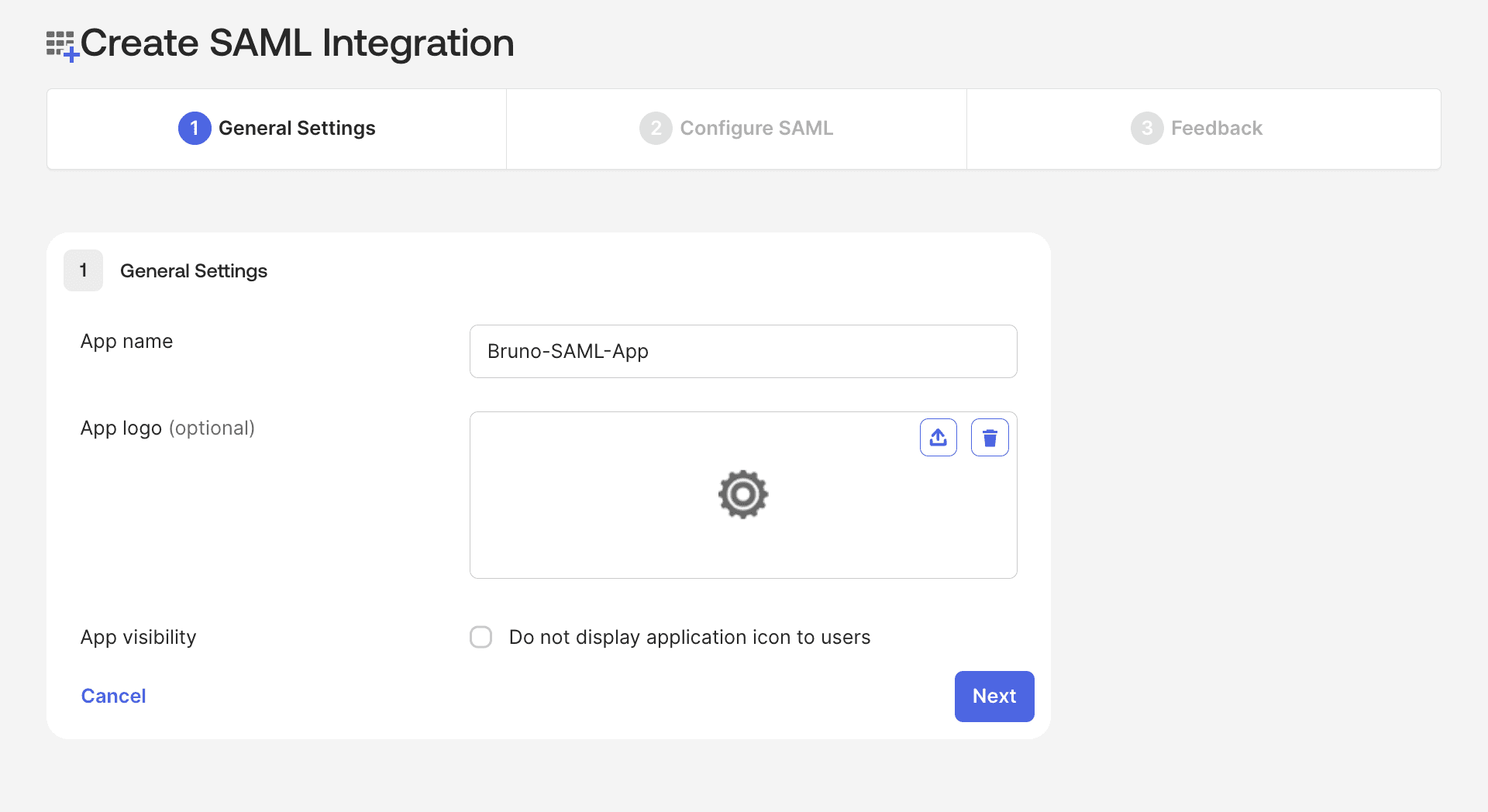
- Enter the following information:
- App name: Set your own unique identifier (e.g.,
Bruno,Bruno-SAML-App, etc.) - App logo: (Optional) Upload Bruno logo
- App visibility: Configure based on your organization’s preferences
- App name: Set your own unique identifier (e.g.,
- Click Next
Step 3: Configure SAML Settings
Copy the values from the Bruno SSO settings page and paste them into your SAML configuration in Okta.
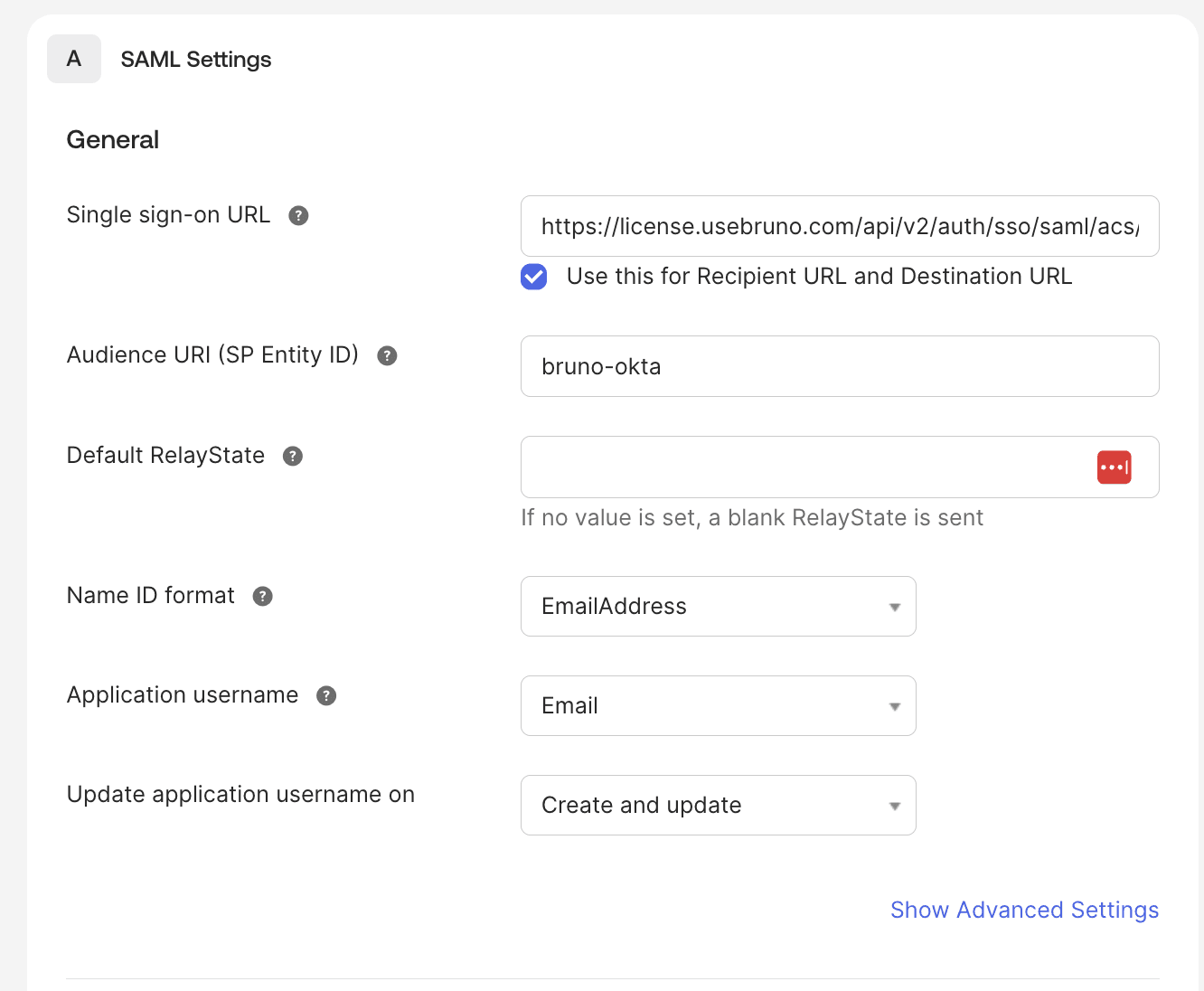
Single Sign-On URL:
-
In the Single sign-on URL field, copy and paste the SAML ACS URL from Bruno
-
Check Use this for Recipient URL and Destination URL
Audience URI (SP Entity ID):
- In the Audience URI (SP Entity ID) field, paste the SP Issuer ID / Entity ID value from the Bruno License Portal
- Important: This value must match EXACTLY what you configured in the Bruno SSO Configuration page
Name ID Format:
- Select EmailAddress from the Name ID format dropdown
Application Username:
- Select Email from the Application username dropdown
Step 4: Configure Attribute Statements
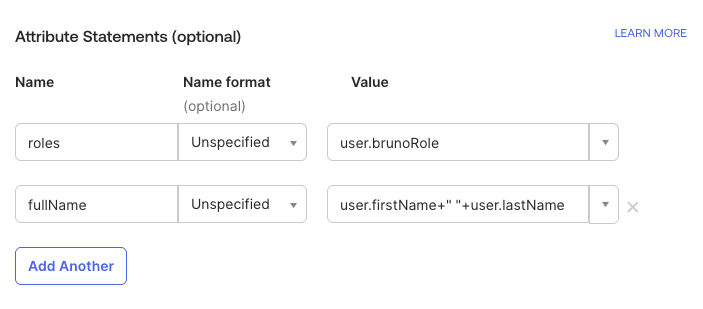
Bruno requires two specific SAML attributes to be configured. Add the following attribute statements:
| Name | Name Format | Value | Notes |
|---|---|---|---|
| roles | Unspecified | Any role value from Okta | Can be a static value (e.g., "admin") or mapped to existing Okta user attributes/groups |
| fullName | Unspecified | user.firstName+" "+user.lastName | Concatenates first and last name. Can also use a single name field if available. |
Configuring the roles attribute:
The roles attribute can be configured in several ways:
-
Static value for testing: Set a hardcoded value like
"admin"for all users assigned to this app- Example: Value =
"admin"
- Example: Value =
-
Map to existing or created Okta user attribute: If your Okta users already have a role attribute or you create a specific attribute for Bruno roles
- Example: Value =
user.userTypeoruser.roleoruser.brunoRole
- Example: Value =
Important: The role value sent by Okta will be mapped to Bruno access levels in the License Portal’s SSO Settings. You’ll configure which role values correspond to admin or user access in Bruno (see Step 2 in the Bruno configuration section below).
Example Scenarios:
- If you set Value =
"Engineering", you’ll addEngineeringto either “Admin Roles” or “User Roles” in Bruno - If you set Value =
user.department, and a user’s department isIT, you’ll addITto the appropriate role field in Bruno
Configuring the fullName attribute:
The fullName attribute can be configured by:
- Concatenating first and last name:
user.firstName+" "+user.lastName - Using a single field if your Okta user profile has a combined name field
- Mapping to any existing user property that contains the full name
Important: Both roles and fullName attributes are required for Bruno SAML SSO to function correctly. The attribute names are case-sensitive and must match exactly as shown.
Preview the SAML Assertion
- Scroll down to the Preview the SAML assertion generated from the information above section
- Click Preview the SAML Assertion
- Verify the generated XML contains the configured attributes:
NameID Format,roles,fullName - Click Next
Step 5: Complete Okta App Setup
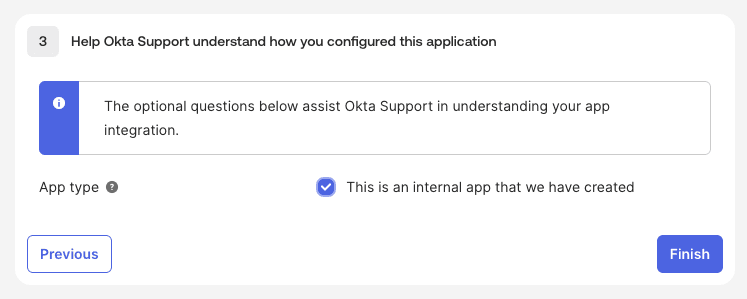
- On the Feedback page:
- Select I’m an Okta customer adding an internal app
- Check This is an internal app that we have created
- Click Finish
Finish SSO Configuration in Bruno
Step 1: Add SSO URL to Bruno License Portal
IdP Login URL / SSO URL
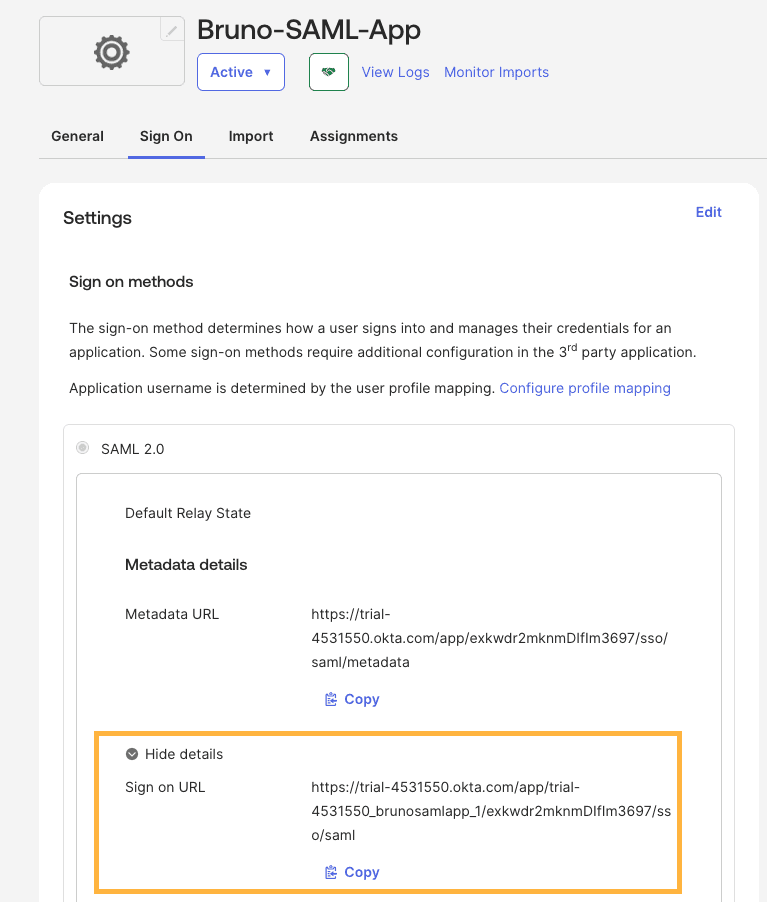
- In your configure Okta application, navigate to the Sign On tab
- Scroll down to the SAML 2.0 section, expand the Hide details section
- Copy the following values (you’ll need these for Bruno configuration):
- Sign on URL: Copy this URL
- Return to the Bruno License Portal tab you opened from the earlier configuration
- Navigate to Settings → SSO (if not already there)
- Under SAML Configuration paste the Sign on URL from Okta into the IdP Login URL / SSO URL field

Step 2: Add IdP Certificate to Bruno License Portal
Okta IdP Certificate
- Scroll down the Sign On tab to SAML Signing Certificates
- Click Generate new certificate
- For the newly generated certificate, click the Actions dropdown and select Download Certificate
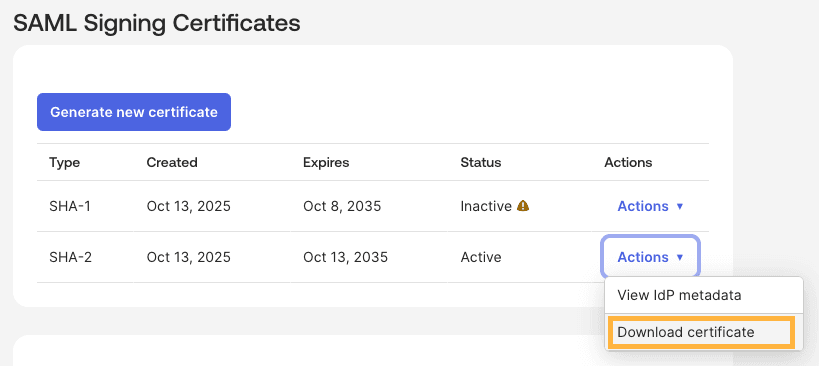
- Open the downloaded certificate file and copy the contents (include the
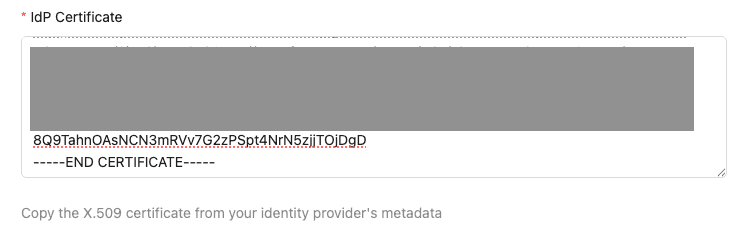
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----lines) - Return to the Bruno License Portal tab you opened from the earlier configuration
- Under SAML Configuration paste the certificate contents into the IdP Certificate field
Step 3: Map the role values from Okta to Bruno access levels
-
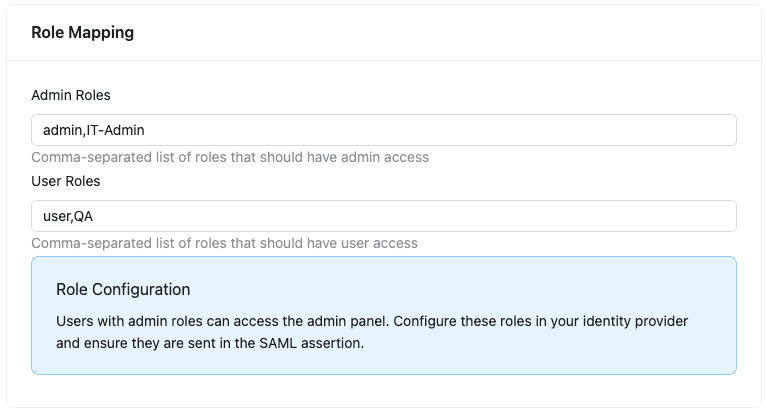
Under the Bruno License Portal in the SSO Configuration page, scroll down to the Role Mapping section
-
Admin Roles: Enter the role values (comma-separated) that should have admin access to Bruno
- Example:
admin,BrunoAdmin,IT-Administrators - These values must match what you configured in the
rolesattribute in Okta - Users with these roles can access the admin panel and manage licenses
- Example:
-
User Roles: Enter the role values (comma-separated) that should have user access to Bruno
- Example:
user,Engineering,Developers,QA - These values must match what you configured in the
rolesattribute in Okta - Users with these roles will be able to activate their Bruno licenses with SSO. They will not have access to the admin panel.
- Example:
How Role Mapping Works:
The role value you configured in Okta’s roles attribute statement will be sent in the SAML assertion. Bruno will check if this value matches any role in the “Admin Roles” or “User Roles” fields.
Example:
- In Okta, you set the
rolesattribute to"Engineering" - In Bruno Admin Roles, you enter:
admin,BrunoAdmin - In Bruno User Roles, you enter:
user,Engineering,QA - Result: Users with the
Engineeringrole are able to activate their Bruno licenses with SSO (matches “Engineering” in User Roles)
Important: Role values are case-sensitive. Ensure the values in Okta’s roles attribute match exactly with the values you enter in Bruno’s Admin Roles or User Roles fields.
Step 4: Configure Session Settings
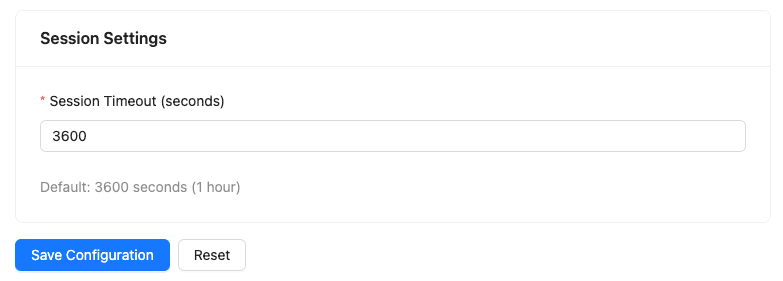
- Scroll down to the Session Timeout section:
- Set the session timeout in seconds (default: 3600 = 1 hour)
- Click Save Configuration to apply your SAML SSO configuration
Test Your SAML Configuration
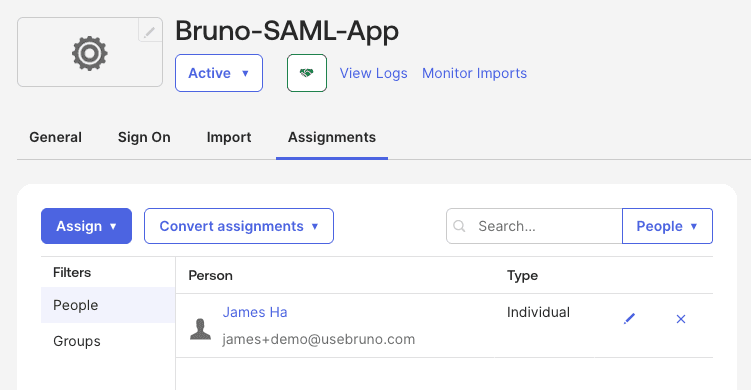
Assign Users or Groups
- In your Okta Bruno application, navigate to the Assignments tab
- Click Assign → Assign to People or Assign to Groups
- Note: Users assigned must already exist in your subscription under the Bruno License Portal in order to login with SSO
- Select the users or groups that should have access to Bruno
- Click Assign and Done
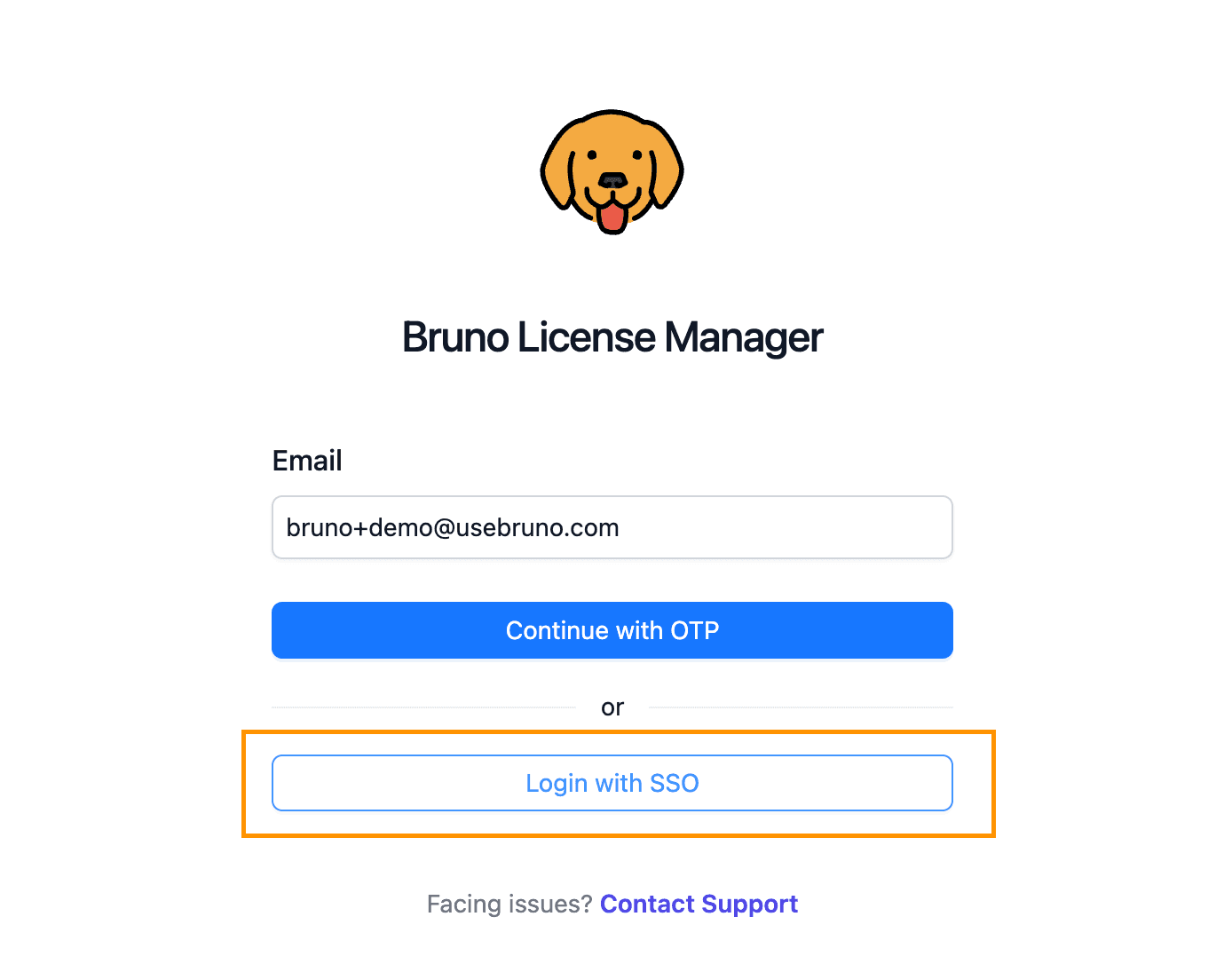
Test SSO Login
- Navigate to the Bruno License Portal (https://license.usebruno.com/ )
- Enter the email address of a user assigned to the Bruno app in Okta
- Click Login with SSO
- You should be redirected to Okta to authenticate
- If your user is an admin in Bruno and contains the correct role mapping, you should be redirected back to the Bruno License Portal
Next Steps
After setting up SSO with Okta, you can:
- Configure SCIM Provisioning to automate user provisioning and deprovisioning
- Manage your Bruno licenses in the License Portal
Related Resources
For more information about configuring SAML SSO and managing attributes in Okta, refer to these Okta documentation resources:
- SAML app integrations - Overview of SAML protocol and Okta SAML applications
- Create SAML app integrations - Step-by-step guide for creating SAML applications in Okta
- Define attribute statements - Configure SAML attribute statements for user attributes and roles
- Define group attribute statements - Map Okta groups to SAML attributes for role-based access control
- Application Integration Wizard SAML field reference - Reference guide for SAML configuration fields
- Build a Single Sign-On (SSO) integration - Developer guide for building SAML SSO integrations